02 March 2019
Reading time: 3 min
There is a well-known expression: who owns information, he owns the world. However, «extracting information» sometimes takes the form of industrial espionage - a terrible horror story, at the mention of which we imagine giant strictly secret factories and foreign agents sneaking among machine tools appear. Certainly in hats pulled over the nose.
In fact, industrial espionage is almost a daily occurrence, it goes with us to work and makes its jiggery-pokery in neighboring garages. And, despite the possible criminal liability for this unworthy act, many people are not averse to earning money in this way. And employers suffer. They have to incur losses and take care of blocking the information «channel».
Our client, by the way, a talented engineer, an active local entrepreneur and just a wonderful person, suffered from such «garage» spies. His company is engaged in designing and producing small breweries with a capacity from 100 kg to 2 tons. Yes, the ones where modern craft beer is brewed. And just good beer at times.
Part 1. Situation: theft of customer base
QUOTE
«You have no idea how hard it is to find a good engineer. I taught all those who work for me now. The technologist was invited from Novosibirsk in general»,- this is how our client began his story, - «I invested in the promotion, in the site. It works, brings us 2-4 clients per month. And one brewery costs from 2 to 8 million rubles».
For each client the designer makes a set of technical documentation, on the basis of which the cost of the brewery is calculated. This is an important part of the story, you'll see why.
In 2015, a businessman discovered that some «competitors» send a commercial offer to their potential customers with their own (!) technical documentation, but all services are 15% cheaper.
QUOTE
«It's clear why it's cheaper — they don't need to develop the site, they don't need to pay designers — just steal documentation and offer it to a client! By the way, this «competitors» work nearby, in the garage, they do everything handicraft. And what kind of competitors are these guys? My former employees! » - the customer complained.
Now you may have thought: «Everything is clear with this case: it is necessary to find a thief and and hand him over to the chief - for all kinds of desecration and the criminal responsibility».
Nothing like this.
QUOTE
«I suspect that one of the designers is transmitting both documentation and information to them. Would I want you to catch the one who does it? No. If you find him, I will not be able to continue working with him. And finding a new employee is extremely difficult. I want you to simply eliminate the possibility of transferring information to competitors», - that was the task of the client.
Since tracking down the «beer spy» forbade his direct boss, and gathering all the employees and threatening them with a massacre prohibited the law, we had to find an elegant solution in our professional sphere.
Part 2. Solution
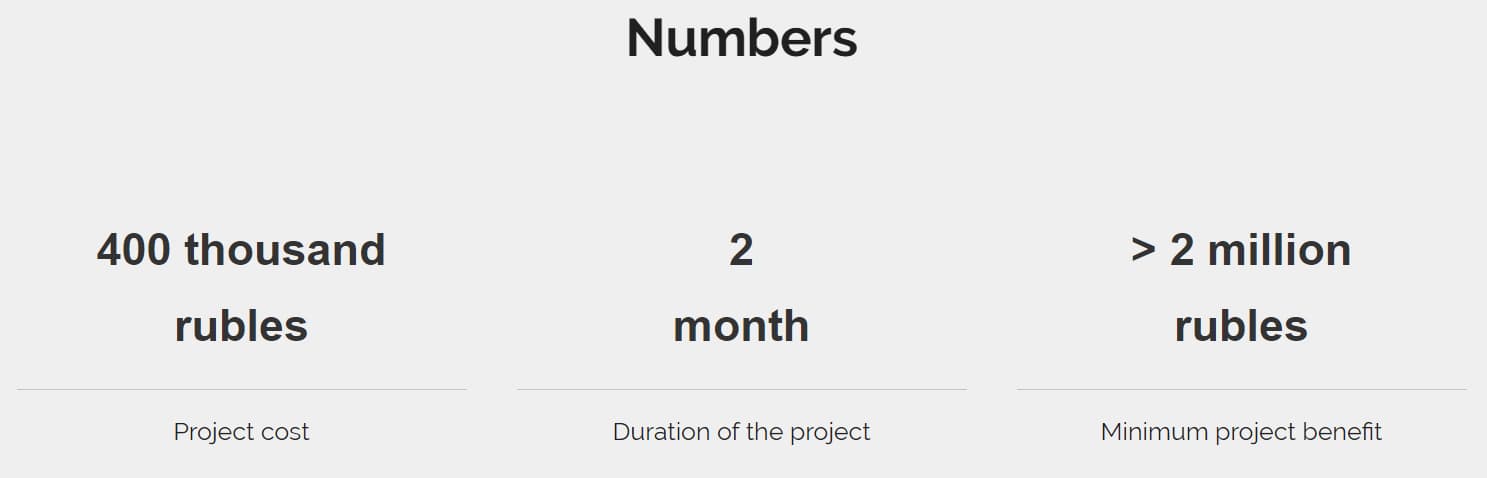
We managed to develop a technical solution that completely satisfied the customer. And now, after three years, it is already possible to draw conclusions about how successful it was: there were no more cases of theft of documentation.
How exactly have we achieved this?
Before our appearance, the company did not seriously think about Internet security. All computers had Internet access, there was no administration policy, and in general, users did everything they wanted. Theoretically, our «beer spy» could be hiding not only under the mask of a designer. In the list of suspects were also all sales managers, because they prepare commercial proposals and, accordingly, have access to the documents.
Then we worked in two directions.
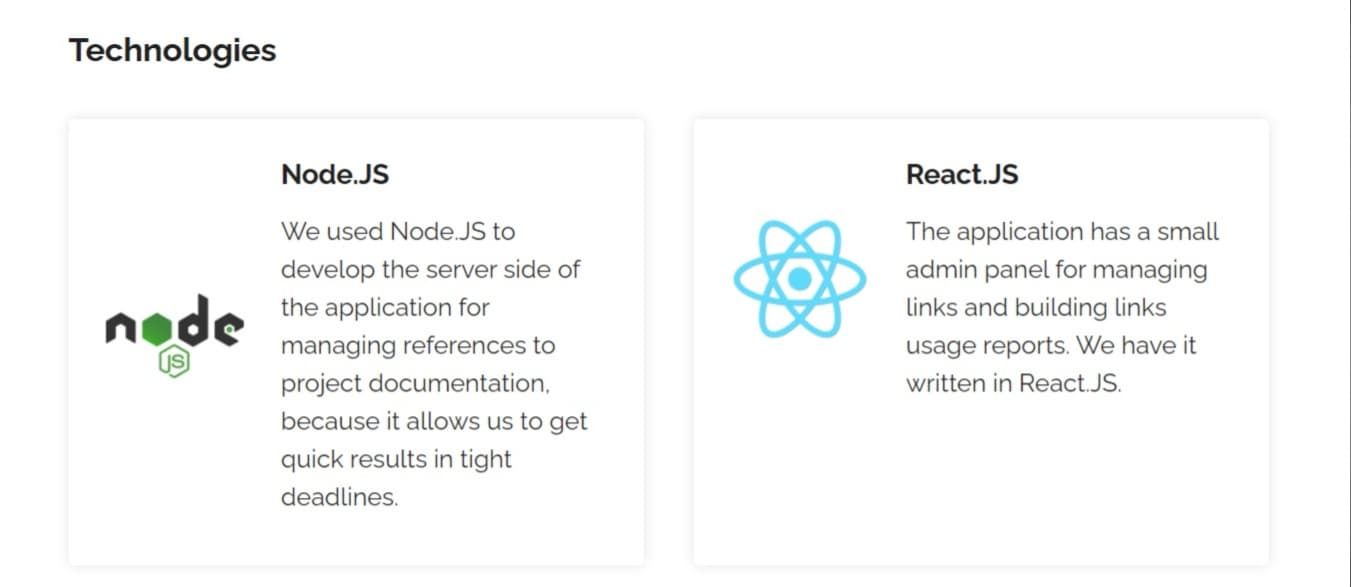
The era of administration has come to the company. A domain controller has been configured on the Windows Server operating system. There was a special account for engineers, on behalf of which it was possible to run the program for creating AutoCAD drawings. In addition to working with the program in this account it was impossible to do anything - it did not have access to the Internet, did not allow copying or writing documents on electronic media. There was only access to files on the network storage where the drawings were saved.
Also each designer had his own personal account, with the help of it he entered the computer, could use the Internet, etc. But these personal accounts, in turn, did not have access to the network drive and AutoCAD. For the most inventive thiefs we even banned the clipboard, in order to exclude the possibility of copying data in one account and pasting into another.
The second part of the solution of the problem relates directly to the sales managers. They lost access to the network drive where the drawings are stored forever. Instead, a web application was written for them using Node.js. This application generated unique links directly to the drawings.
Now, if the sales manager needed to attach documents to the commercial offer, he could use the application to generate a link to all the necessary drawings. The link contained information about who its creator was and when it was created, even if several different employees referred to the same source. In turn, if a user requested a document by reference, the system recorded its IP, location, time at which he entered the disk, and the number of times.
Part 3. Results
This set of solutions made the theft of documentation impossible — the engineers simply lost the opportunity to pull it out of the company, and the managers were under constant supervision.
About the project
QUOTE
«It was a simple project, but we solved the problem in a rather unusual way. We worked about 1-2 months. The cost of the work is about 300,000 rubles (by the way, it was 2015). In this case, we helped the client save a significant amount. If we suppose that the company receives orders at least 2-4 times a week, and the cost of each is from two million rubles (once again, data for 2015) is easy to count how useful our solution was. Our link management application has come in handy in the future as well. It turned into a small project called Lynx.land. The mechanism is the same as in this case, but the idea is slightly different. For example, a company places a link to an article on the web. Using this application, you can customize it so that different information will be shown to audiences from different cities - you can set up a redirect for various target groups using various methods without creating a huge number of unnecessary links that will confuse everyone. First of all, we now use this interesting solution for ourselves, but it is useful for a wide audience.»
read more